I just found a client facing this problem, that his website is attacked by a some kind of virus or malicious script. His website is replaced and redirects to another malicious web pages, some random and malicious blog posts generated on his posts list containing harmful links, etc.
After checking further, I found that many of php files in his website database has this few lines of malicious script:
if($_SERVER[“SCRIPT_NAME”] != “/index.php”){ header(“HTTP/1.0 403 Forbidden”);echo base64_decode(“PCFET0NUWVBFIEhUTUwgUFVCTElDICItLy9JRVRGLy9EVEQgSFRNTCAyLjAvL0VOIj4KPGh0bWw+PGhlYWQ+Cjx0aXRsZT40MDMgRm9yYmlkZGVuPC90aXRsZT4KPC9oZWFkPjxib2R5Pgo8aDE+Rm9yYmlkZGVuPC9oMT4KPHA+WW91IGRvbid0IGhhdmUgcGVybWlzc2lvbiB0byBhY2Nlc3MgdGhpcyByZXNvdXJjZS48L3A+Cjxocj4KPC9ib2R5PjwvaHRtbD4=”);die(); }
To solve this problem, I must replace all the files inside his WordPress installation directory with the original ones, because existing files are modified by the virus. Also I make sure that I disable all the plugins first, then check which plugin contains the original virus.
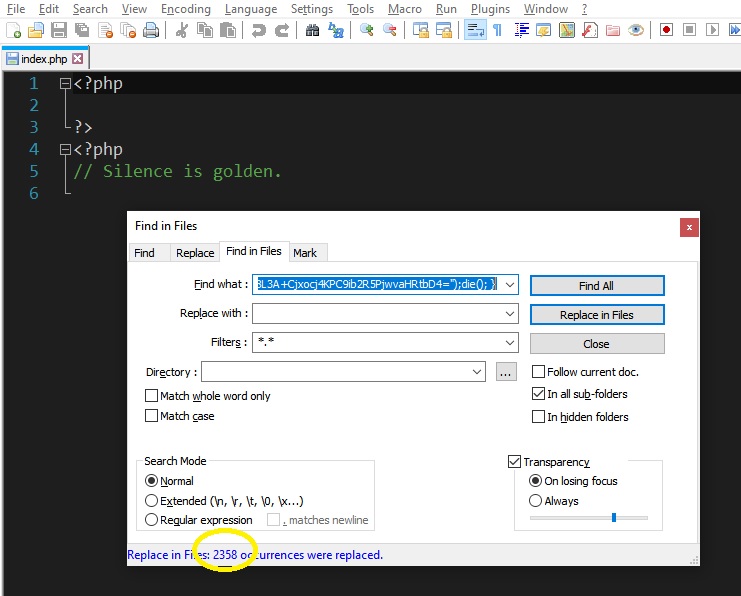
As you can see from this screenshot, there was 2358 replacements in WP plugins directory only!
Also another thing, check any htaccess files, most of them are generated by the virus and you better remove them.
The content of those htaccess files are this:
<FilesMatch “.*\.(py|exe|phtml|php|PHP|Php|PHp|pHp|pHP|phP|PhP|php5|suspected)$”>
Order Allow,Deny
Deny from all
</FilesMatch>
<FilesMatch “^(epvefu.php|ptgswf.php|wp-dbevm.php|wp-zekmg.php|moni-inai.php|moni-tjsd.php)$”>
Order Allow,Deny
Allow from all
</FilesMatch>
Hope this post useful to you. Thanks!